ENS Joseph P. Bunyard
USNA 2020 Voices of Maritime History Prize Essay
Executive Summary
Question
How can the United States Department of the Navy (DoN) continue to leverage its advantages in Network Centric Warfare (NCW) in a communications contested environment?
Key Points
A return to great power competition places a renewed emphasis on network survivability, which is essential to the prosecution of modern naval warfare against near-peer adversaries with high-end capabilities. Current and evolving DoN strategies depend on fragile network connections that are increasingly vulnerable to enemy denial or disruption. The Battle of Britain offers key insights, from which DoN can benefit, into leveraging integrated network technology to achieve operational outcomes.
Methodology
This paper uses historical examples and open source information to illustrate the role of networks in naval warfare, describe their vulnerabilities in a communications contested environment, and propose a way ahead.
Recommendations
DoN must invest in infrastructure that is more advanced, defensible, and autonomous in order to outpace the growing threat to Navy networks and the myriad of systems that depend on them. Key lines of effort must include keeping pace with rapidly evolving computing capacity, increasing network resilience through node surge capacity, and hardening existing electronic lines of communication.
I. Network Centric Warfare
Since the age of sail, networks have included both the physical and conceptual lines of communication necessary to relay information on the operational and strategic level. While these networks once consisted of signal flags, couriers, and telegrams, today’s requirement for real-time over-the-horizon communication necessitates methods of exceptional complexity.
Modern networks enable the global Command, Control, Communications, Computers, Intelligence, Surveillance, and Reconnaissance (C4ISR) infrastructure the Navy and Marine Corps rely on for everything from munitions guidance to transoceanic navigation. The act of leveraging networks for operational purposes is known as Network Centric Warfare (NCW), which is divided into three domains: the surface layer for battlefield local area networks, the airborne layer providing theatre wide coverage, and the space level for the Navy and Marine Corps Global Command and Control System (see Figure 1). 1 The 2016 Navy Network Environment Strategy (NNES) defines these networks as the “basic operational backbone” for all forms of communication and data processing. 2
In the current era of renewed great power competition, near-peer rivals openly flaunt the means and motivation to deny sailors and Marines the “overwhelming war-fighting advantage” uncontested network access provides. 3 Leading up to the Battle of Britain in 1940, the United Kingdom drastically shifted from expeditionary low-intensity conflict in foreign colonies to high-end warfare against Nazi Germany. The Department of the Navy (DoN) must now prepare for near-peer conflict much in the same way the UK did at the onset of the Second World War—by securing network access in both the electronic and physical battlespace.
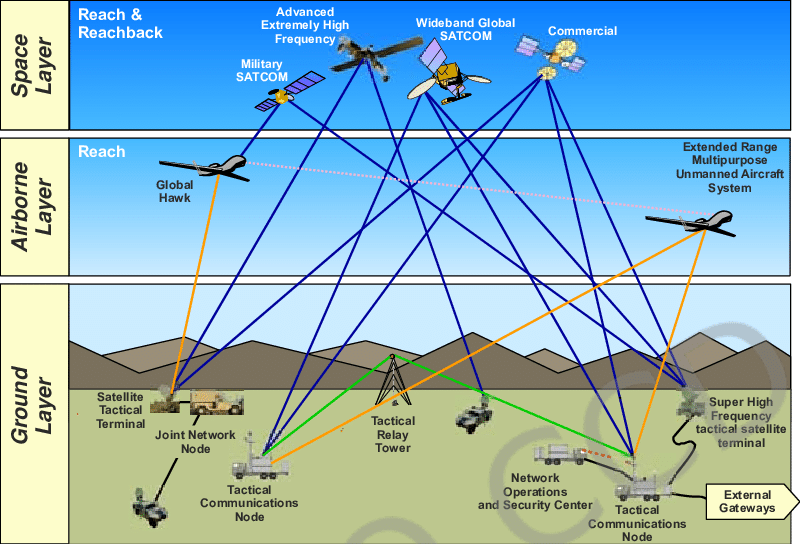
Figure 1-Model of DoN assets deployed as nodes in NWC 4
I. Networks in Modern Naval Warfare
The future of naval warfare depends on reliable network access in the backyard of adversaries motivated to deny it. As the Navy and Marine Corps transition to a more distributed, automated force, the ability to connect sensors, command and control platforms, and shooters will be of the utmost importance. 5
A Strategic Shift
Distributed maritime operations represent the future of naval warfare by encompassing the collective efforts of the Navy and Marine Corps to deploy smaller, increasingly integrated forces in place of traditional strike groups. In its 2017 Surface Force Strategy (SFS), the Navy coined this requirement to send more ships further, faster, and more frequently into contested environments “distributed lethality.” 6 The Marine Corps’ 2019 Commandant Planning Guidance expands on the “distributed lethality” concept by insisting that forward deployed “naval expeditionary forces” with “sufficient resilience to persist within the weapons engagement-zone once actively contested” are critical to sea-denial and sea control. 7 An integrated naval force that is smaller and further apart will require robust networks capable of maintaining C4ISR and network-dependent weapons and countermeasures in a communications contested environment. Ensuring the availability of these systems is vital to carrying out the three critical functions of distributed maritime operations. In the third edition of Fleet Tactics and Naval Operations, the late renowned naval strategist CAPT Wayne Hughes, USN (Ret), lists these critical functions as dispersing assets for multi-node scouting and strike warfare, out maneuvering an adversary, and massing forces for defensive measures. 8
Scout and Mass
According to the Navy’s 2016 Force Structure Assessment, the reemergence of near-peer competitors will require 148 new small surface combatants and 110 unmanned surface vessels to counter worldwide challenges to US sea lines of communication. 9 Many of these challenges come in the form of maritime insurgencies in places like the South China Sea and the Persian Gulf. Here, sustained patrols—for which current Navy platforms are ill-suited—are key to ensuring respect for international law. 10 Deploying a greater number of smaller platforms requires a network capable of massing ships and over-the-horizon capabilities when DoN presence is contested, in order to compensate for the reduced individual capability of smaller combatants—relative to that of a Cruiser or Destroyer (CRUDES). The NCW-enabled ability to patrol independently and mass overwhelming force when contested is vital to maintaining a credible deterrence.
Strike
The benefits of a smaller, distributed force are not exclusive to countering maritime insurgencies. The mathematical formulas from Fleet Tactics and Naval Operations in Figure 2 below illustrate the superior combat power of smaller, networked ships compared to larger, traditional surface combatants in a Mahan-styled decisive battle. 11 However, these hypothetical scenarios fail to represent the critical vulnerability of distributed maritime operations. Dispersed forces are only as capable as the networks that connect them. The value of connectivity increases as unmanned, optionally, and optimally manned platforms replace sailors and Marines on the front lines. 12
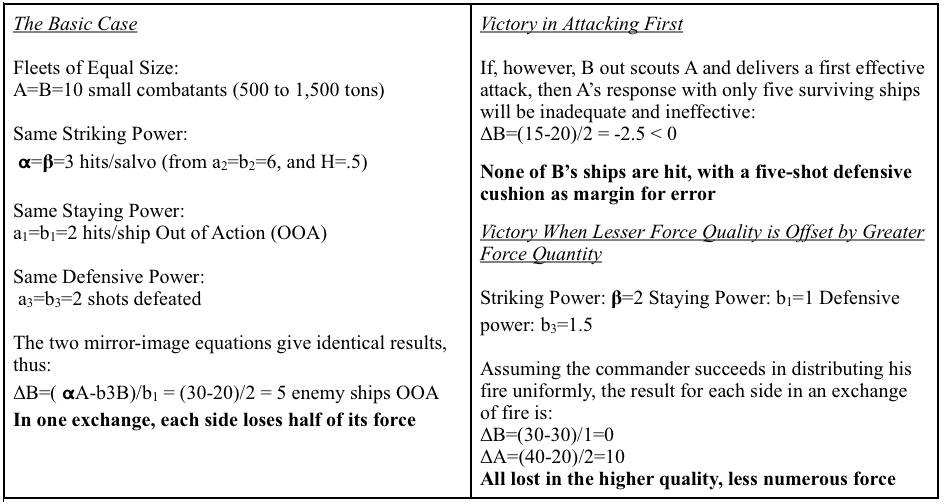
Figure 2-Selected excerpts from Fleet Tactics and Naval Operations, Third Edition 13
Out Maneuver
Maneuvering dispersed assets across a wide operating area forces an adversary to solve the complex, resource heavy problems of finding, tracking, and targeting each individual combatant, as opposed to a large formation. 14 However, dispersing assets while maintaining network access requires commanders to choose between the increased electromagnetic signature associated with C4ISR tasks or limiting emissions to avoid enemy detection. 15 As the Navy and Marine Corps introduce greater numbers of unmanned, optionally, and optimally manned platforms to the battlespace, the viability of NCW inside of an enemy’s weapons engagement zone will depend on the ability of commanders to both secure and mask their electronic emissions while maintaining network access (see Figure 3).
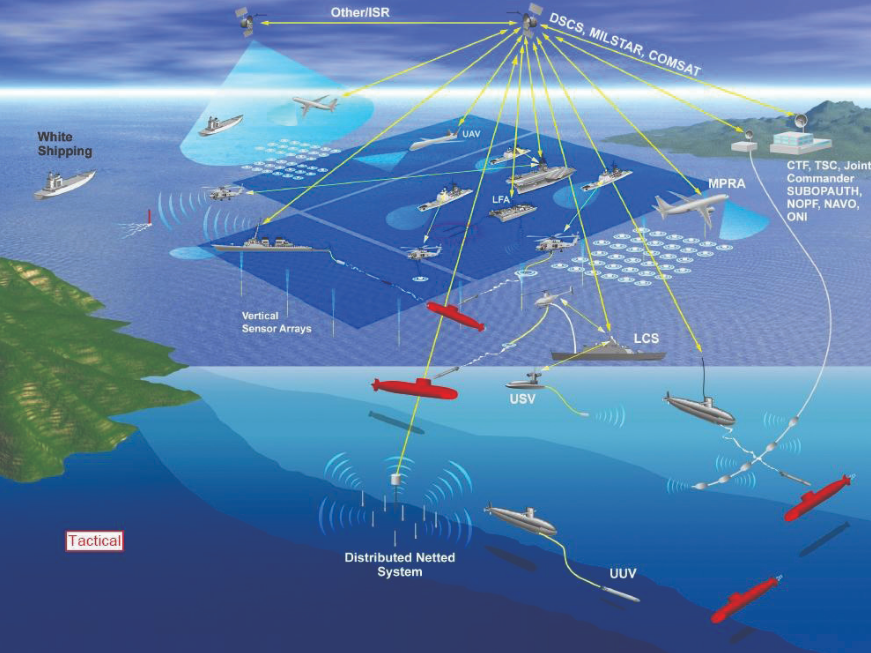
Figure 3-Modern C4ISR Infrastructure Integrated with Unmanned Vehicles 16
II. Vulnerabilities
A return to great power competition exposes DoN networks to threats unique to near-peer adversaries, which the Navy and Marine Corps have not been forced to address in the post-Cold War era. 17 Chief among these threats are Anti-Satellite (ASAT) and Electronic Warfare (EW) methods the Pentagon accuses China and Russia of designing “explicitly to deny, degrade, deceive, disrupt, or destroy America’s eyes and ears in space.” 18
Anti-Satellite Warfare
Great power competition elevates the threat of ASAT missile strikes by near-peers and their proxies. Both China and Russia openly flaunt their ASAT missile capabilities through provocative shows of placing and destroying satellites in close vicinity to US intelligence assets. 19 Perhaps even more inflammatory—according to a 2020 Congressional Research Service report by Kenneth Katzman—China and Russia actively share ballistic missile technology and expertise with Iran and North Korea, effectively working to give even regional powers the ability to affect DoN’s operations globally. 20 A single ASAT strike would have catastrophic consequences for DoN networks. Defense industrial base estimates indicate that even a satellite with common commercial capabilities would take the Department of Defense approximately three years to replace. 21
ASAT warfare is not limited to missile strikes. Russia and China are actively investing in satellites capable of disabling other satellites with “little to no fanfare.” 22 Such satellites are equipped with nets, robotic arms, fuel draining apparatuses, and potentially even directed energy weapons, under the pretense of controlling “space-junk.” 15 In reality, they provide potential adversaries the ability to disrupt a satellite’s operation by physically interacting with it in space, unbeknownst to operators on the ground. Given the lack of treaties governing how and where satellites may deploy, malicious actors can even pre-position such assets in close proximity to US satellites—as Russia and China have demonstrated—in order to initiate attacks with little to no warning. 24
Electronic Warfare
The spoofing and jamming of GPS signals poses an entirely different risk to DoN’s ability to conduct warfare. Spoofing is the act of directing false data—in the case of GPS, coordinates and time—to a receiver with the intention of misguiding its platform. 25 Jamming occurs when a bad actor sends more power to a receiver on its operating frequency than the amount of power received from its intended source with the goal of degrading the system’s ability to operate (see figure 4). Unlike traditional military forces, EW is not constrained by vast geographic buffers, like the Pacific Ocean, from which the US historically benefits. According to a recent report by the Congressional Research Service, the international reach of Huawei and ZTE 5G networks amplifies the threat of Chinese EW by providing infrastructure abroad that could quickly be repurposed for spoofing, jamming, and signals intelligence. 26
“Smart spoofing” allows malicious actors to guide semi and fully autonomous ships, aircraft, and weapons systems off course by sending their receivers inaccurate GPS coordinates. 27 Today, few navigation systems are equipped with the means to scrutinize the validity of the GPS signals they receive. 28 When used against GPS guided munitions, “smart spoofing” can easily make weapons inoperable, or worse, it can redirect them from a legitimate target—like an enemy’s air base—to an unintended site, such as a hospital. 29 Due to the exceptional distance between satellites and receivers on the surface, GPS signals are weak enough to be spoofed by nearly anyone with internet access and an off-the-shelf transmitter. 30
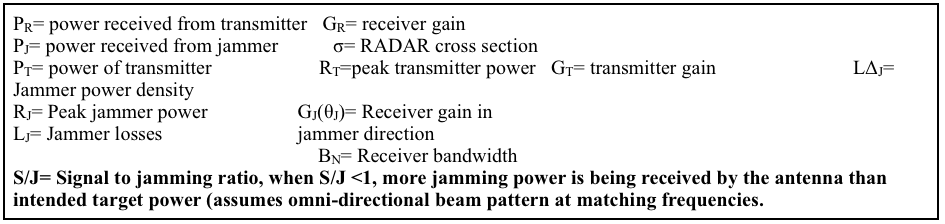
Figure 4-RADAR jamming equation 31
Signal jamming and spoofing pose a heightened risk to the type of unmanned assets the Navy and Marine Corps are introducing in growing numbers to the battlespace. In 2011, Iran claimed that it used jamming and “smart spoofing” techniques to hijack and safely land an American Unmanned Aerial Vehicle (UAV) in Iranian territory. 32 As Figure 4 above illustrates, such results are possible due to the critical role that relative distance plays in signal strength. Since transmitter power is subject to the inverse square law, there is little that ships and aircraft can do to prevent RADAR and communications “burn through” in potential hot spots such as the South China Sea and the Persian Gulf. In order to preserve the warfighting advantages of NCW in the littorals, DoN must invest in advanced, defensible networks that maintain resiliency in close proximity to enemy assets, including commercial 5G infrastructure made in China.
III. Historical Analogy
Robust networks are force multipliers. The UK’s investment in an advanced anti-air network ahead of the Battle of Britain enabled it to halt the seemingly unstoppable Luftwaffe, securing the staging grounds for the Allies’ liberation of Europe. The keys to this feat were a forward-thinking approach towards integrating new technology into existing systems and a substantial investment in advanced infrastructure to maximize network effectiveness.
Although often derided as “cowardly” for his policy of appeasement towards Nazi Germany, Neville Chamberlain led an unprecedented overhaul of the Royal Air Force (RAF) between his infamous 1938 meeting with Hitler in Munich and the start of the Battle of Britain in 1940. Shocked by the speed and intensity of the Blitzkrieg, Chamberlain believed that the key to defending the British Isles would be to “push forward [its] defense” through air superiority that only fighters could provide. 33 Securing investment for the new Spitfire and Hurricane interceptors would require Chamberlain to upend a long revered bomber-centric strategy—known as the “Trenchard Doctrine”—which claimed that such fighters were “an irrelevance” in what was then an entirely offensive air force. Despite fierce objections from Parliament and the Air Staff, in November 1938, a mere five weeks after promising Britons “peace in our time,” Chamberlain’s cabinet launched “Scheme M,” an ambitious plan that increased the strength of the RAF’s Fighter Command ten-fold by the start of the Battle of Britain. 34
While Germany—thinking that the war was nearly won—all but abandoned RADAR research and development in the lead up to the Battle of Britain, Chamberlain doubled-down on the new technology. Investing heavily in “Chain Home” early warning stations along the English and Scottish coasts gave the RAF the ability to pinpoint imminent air raids deep into Nazi controlled territory. 35 However, with little ability to link Chain Home information to RAF squadrons at the beginning of the war, only 30% of pilots ever saw a German aircraft during a given intercept mission. 36 To solve this problem, the UK implemented the “Dowding System,” a game-changing C4ISR network enabling the quick reception, verification, organization, and dissemination of target data—increasing interception rates to over 90% by the end of the three-month-long Battle of Britain. 15
The Dowding System linked coastal Chain Home stations with inward-looking Royal Observer Corps spotters—often stationed aloft telephone poles—to transmit real-time information on the number, direction, and location of enemy bombers to Fighter Command Headquarters (FCHQ) throughout a given raid. 38 FCHQ maintained an overall picture of the raid, notifying potential targets of an imminent attack, and pushing intercept information down to the specific squadrons tasked with the defense of the relevant sectors. 15 With this information, RAF squadrons often had the luxury of choosing when, where, and with what number of fighters to engage enemy formations. The warfighting advantage the Dowding System afforded the RAF allowed it to achieve an average two-to-one kill-to-death ratio against superior Nazi fighter planes over the course of the campaign, despite beginning the Battle of Britain with half as many aircraft as the . 40
The quality of targeting information passed on to RAF fighters depended on the coherence, accuracy, and speed of the Dowding System. “Filter Rooms” located next to segments of Chain Home for which they were responsible provided the quality assurance needed to make the Dowding System effective by verifying, interpreting, and plotting RADAR returns. 41 Slow or unreliable information did not simply cause fighters to miss their intercepts; it caused the RAF to waste limited assets that could have otherwise been effectively deployed.
The need to communicate information as quickly as it could be generated spurred a massive investment in telecommunications infrastructure across the UK. From the time a “Filter Room” received a RADAR return from Chain Home, it took 25 seconds to plot it, five seconds to determine the contact’s vector, and 30 seconds to transmit the information across an extensive network of telephone cables connecting coastal RADAR stations and far-flung aviation squadrons to FCHQ. 42 If the RAF aircraft in the sector called upon to intercept the target were in a state of “readiness,” they could be deployed with target data in-hand a mere six-and-a-half minutes after a contact’s first detection—long before Nazi bombers arrived over British territory. 43
The UK’s investment in Chain Home and its accompanying C4ISR network yielded unexpected dividends in the form of signals intelligence. By 1940, the construction of imposing RADAR stations along its southern coast allowed the UK to intercept “virtually every radio transmission of the German forces within range.” 15 The effective implementation of the Dowding System meant the network necessary to exploit this intelligence in real-time was already in place. In fact, RAF pilots often had German raid orders in their hands less than an hour after their transmittal. 45 The inability of the Nazis to keep pace with British research, development, and implementation of the Dowding System and its supporting infrastructure is a clear example of how abdicating primacy in NCW cedes unknown advantages to one’s adversaries.

Chain Home RADAR stations 46
The Dowding System provided the UK an unprecedented advantage in what renowned military strategist Air Force Colonel John Boyd would later call the Observe, Orient, Decide, Act (OODA) loop. According to Boyd, the combatant with the shortest OODA loop has a decisive advantage in warfare, putting them on “the proper side of fighting.” 47 Boyd’s OODA framework expanded on an assessment made 70 years earlier by Prussian General Helmuth von Motlke, who attributed his success in the Franco-Prussian War of 1870 to a “systems based approach.” Motlke believed that as the character of warfare “broadened” with new means of communication and transportation, the combatant with the quickest and most reliable C2 network would be able to exploit the rapid changes and unknown factors in warfare in order to seize victory at the operational level. 15
Evaluating the Battle of Britain through the theories of Boyd and Motlke provides key insights into how DoN conducts modern day network centric warfare. NCW not only provides an asymmetric advantage by improving C4ISR, as in the Battle of Britain; it also represents a domain of continuous competition in which DoN must maintain the fastest and most accurate C2 networks. As Boyd and Motlke explain, the combatant with the most capable C2 system wields a decisive advantage in warfare.
The home field advantage the RAF received during the Battle of Britain by way of the Dowding System meant that fighters had only one role—shooter. This is an advantage China is likely to wield in maritime hot spots like the South China Sea and the Strait of Taiwan. Competing globally with near-peers in a new era of great power competition requires DoN assets to bring the network necessary to close their OODA loops and kill chains with them to the battlespace. Mimicking the detection, verification, prioritization, and tracking of enemy assets that the Dowding System offered the RAF in a modern day communications contested environment requires networks with a broad reach, electronic warfare contingencies, and an unprecedented amount of computing power. Depriving the fleet of any of these characteristics would be to remove Chain Home or the Royal Observer Corps from the Dowding System—significantly limiting its function and allowing the enemy to remain unseen until he is that much closer to his objective. DoN’s ability to outpace the ASAT and EW capabilities of its potential adversaries through early investment and fleet integration will determine whether it will play the role of the RAF or the Luftwaffe in the next near-peer conflict.
IV. Recommendations
As tensions rise between the US and China, warnings of Thucydides’ trap have become a common refrain among those who believe the two superpowers are “destined for war.” 49 Returning to great power competition means that DoN must reprioritize its ability to conduct high-end warfare. In 1938, the Chamberlain government—facing a similar situation—answered this call with an unprecedented campaign to overturn conventional thinking, invest heavily in emerging technology, and fully leverage the Dowding System by integrating it with the RAF.
Just as Chamberlain studied the Blitzkrieg and adapted his forces before the Battle of Britain, so has China’s People’s Liberation Army (PLA) studied US post-Cold War operations. As a result, the PLA’s foundational theory of victory, known as “system destruction warfare,” is designed around the notion that success belongs to “the belligerent that can disrupt, paralyze, or destroy the operational capability of [its] enemy’s operational system” through both “kinetic and nonkinetic strikes” while simultaneously “employing a more robust, capable, and adaptable operational system of its own.” 50 Countering Chinese efforts to dismantle and replace the networks sailors and Marines depend on to close the OODA loop requires DoN to take the following steps towards building a more robust infrastructure.
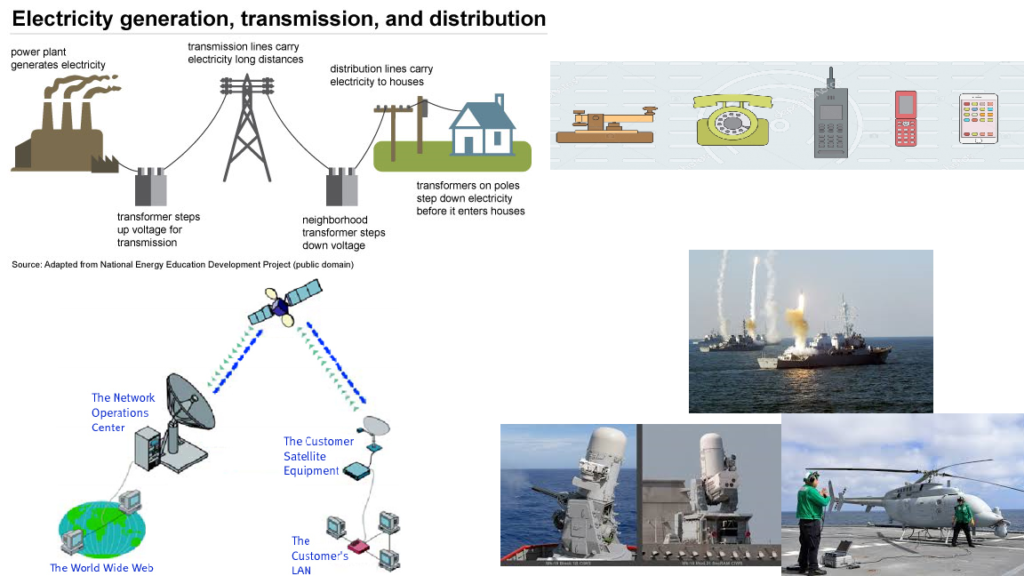
Figure 5-Legacy components of electrical grids and Navy networks (left) juxtaposed with examples of the increasingly complex systems they support (right) 51
In a recent Forrestal Lecture at the US Naval Academy, former Supreme Allied Commander Europe, Admiral James Stavridis, USN (Ret.), used the example of Alexander Graham Bell and Thomas Edison attempting to recognize the modern iterations of their respective inventions in order to demonstrate the underlying vulnerability of flashy technology running on outdated systems. While the phone has evolved to a mobile device with a worldwide reach and internet accessibility, the electrical grid used to charge it has evolved relatively little from Thomas Edison’s original designs for New York City (see Figure 5). 52 As a cellphone is relatively useless without an electrical grid to charge it, so are assets such as Tomahawk Land Attack Missiles without a C4ISR network.
In order to maintain a robust network under physical and electronic fire, DoN must build surge capacity into its arsenal of network relays. The ability to rapidly deploy groups of unmanned surface vehicles, UAVs, and miniature satellites across the ground, airborne, and space network layers (see Figure 1) generates the same complex, resource heavy targeting problems for adversaries as distributed maritime operations. However, unlike distributed maritime operations, quantity of assets cannot substitute the quality of bandwidth and computing power that is necessary to link platforms, download data, and process solutions.
In order to support increasingly sophisticated weapons and ISR platforms, DoN must invest in on-board computing power that enables C2 platforms to act as the “Filter Rooms” of the fleet by transforming large amounts of raw data into actionable intelligence for shooters. Just as the Dowding System’s “Filter Rooms” relied on telephone cables out of enemy reach to transmit target information to FCHQ and the Royal Observer Corps, distributed maritime operations requires secure lines of communication that can handle mass amounts of data on enemy weapons systems of increasing sophistication, range, and stealth. In order to ensure the flow of information across the battlespace, the Navy needs a bigger pipe that is harder for the enemy to break.
While—much like the RAF in 1938—DoN may not be able to predict what future advantages investing early and often in network resiliency may yield, it cannot afford to be left behind by near-peers who are willing to make such investments. The 2017 National Security Strategy articulates the challenge of constant improvement in describing the current “non-binary” state of “constant competition” in which the US must seek “overmatch.” 53 Pursuing “overmatch” means DoN cannot simply rely on full-scale EW negatively affecting all combatants equally—similar to how the “Trenchard Doctrine” viewed strategic bombing.
Moore’s law states that “the basic computing power of cutting-edge chips doubles every 24 months as a result of improved processor engineering.” 54 These chips play a vital role in training algorithms to receive, crunch, and transmit data faster than any human. Just as Nazi Germany failed to keep pace with the technological advancements of the UK in the lead up to the Battle of Britain, a failure to regularly invest and integrate rapidly improving network technology could result in deadly disparities between the speed with which DoN can close its OODA loop versus that of its adversaries.
Ensuring DoN’s ability to conduct NCW in a communications contested environment requires networks that are more advanced, defensible, and autonomous. Innovating and integrating new technology in the pursuit of more defensible networks must be a continuous process that outpaces the evolving threats DoN faces. The UK achieved operational overmatch against the Luftwaffe by strategically leveraging innovative technology. If DoN is to fully leverage its warfighting advantage against near-peer rivals, it must continually reinforce the underlying network infrastructure on which it relies.
(Return to December 2020 Table of Contents)
Footnotes
- David Steensma, Global command and control system joint operation planning and execution system § (2003). ↩
- Naval Networking Environment: Strategic Definition, Scope and Strategy § (2016). ↩
- Clay Wilson, Network Centric Warfare: Background and Oversight Issues for Congress. CRS Report for Congress § (2005). ↩
- “Simplified Model of a NCW Information Network Navy and Air Force.” Research Gate. Accessed January 26, 2020. ↩
- Wayne P. Hughes and Robert Girrier, Fleet Tactics and Naval Operations, (Annapolis, Maryland: Naval Institute Press, 2018), 5. ↩
- Thomas Rowdan, ADM USN, Commander of Naval Surface Forces, Surface Force Strategy: Return to Sea Control. Washington, DC, 2017, 9-10. ↩
- David H. Berger, Gen.USMC, 38th Commandant’s Planning Guidance § (2019), 13-14. ↩
- Hughes, 288. ↩
- USNI Staff, “FSA Executive Summary,” USNI News (US Naval Institute, December 16, 2016), https://news.usni.org/wp-content/uploads/2016/12/FSA_Executive-Summary.pdf. ↩
- Hunter Stires, “The South China Sea Needs a ‘COIN’ Toss,” Proceedings, May 2019. ↩
- Hughes, 42, 286. ↩
- John R. Hoehn, and Kelley M. Slayer, Congressional Research Service. National Security Implications of Fifth Generation (5G) Mobile Technologies, § (2020), 1-2. ↩
- Hughes, 277-278 ↩
- Ibid., 279-280. ↩
- Ibid. ↩
- John Grady, “Entire Navy Tomahawk Missile Arsenal Will Upgrade To Block V.” USNI News, January 22, 2020. ↩
- Erik E. Mueller, (2020, April/May). Asymmetric Warfare. Retrieved August 27, 2020, from https://www.rand.org/topics/asymmetric-warfare.html ↩
- Robert S. Walker, and Peter Navarro, “Op-Ed: Trump’s Space Policy Reaches for Mars and the Stars.” SpaceNews.com, October 20, 2016. ↩
- Carin Zissis, “China’s Anti-Satellite Test.” Council on Foreign Relations, February 22, 2007. https://www.cfr.org/backgrounder/chinas-anti-satellite-test; Chelsea Gohd, April 16, 2020. “Russia tests anti-satellite missile and the US Space Force is not happy.” Retrieved August 27, 2020, from https://www.space.com/russia-anti-satellite-missile-test-2020.html. ↩
- Kenneth Katzman, Congressional Research Service. Iran’s Foreign and Defense Policies, § (2020), 14. ↩
- Davis Satellite, AEROSPACE REPORT NO. ATR-2015-0053, How Long Does it Take to Develop and Launch Government Satellite Systems? ↩
- Brian G. Chow, and Henry Sokolski, “Growing U.S. Satellite Vulnerability: The Silent ‘Apocalypse Next’.” SpaceNews.com, August 23, 2018. ↩
- Ibid. ↩
- Brian G. Chow. ↩
- Paul Y. Montgomery, and Todd E. Humphries, “A Multi-Antenna Defense: Receiver-Autonomous GPS Spoofing Detection,” 2019. ↩
- John R. Hoehn, and Kelley M. Slayer, 2. ↩
- Dana Goward. “Now Hear This – ‘Misnavigation’ or Spoofing?” Proceedings, April 2016. ↩
- CAPT Paul Heim, USN (Ret.), WR Systems Director of Strategic Engagement. Interview by author. In person at the 2020 Surface Navy Association Symposium. Washington, DC, January 14, 2020. ↩
- David Hambling, “Ships Fooled in GPS Spoofing Attack Suggest Russian Cyberweapon.” New Scientist, August 10, 2017. ↩
- Dana Goward. ↩
- “Electronic Warfare Reference Guide,” Raytheon.com (Raytheon), accessed February 15, 2020, https://www.raytheon.com/sites/default/files/capabilities/rtnwcm/groups/public/ documents/content/ew-quick-guide-pdf.pdf. ↩
- Greg Jaffe and Thomas Erdbrink, “Iran Says It Downed U.S. Stealth Drone; Pentagon Acknowledges Aircraft Downing,” The Washington Post, December 4, 2011. ↩
- Kyle D. Johnson, “British Appeasement 1936-1939: The Debate between Parliament and the Public,” (2017) https://digitalscholarship.unlv.edu/cgi/viewcontent.cgi?article= 1134&context=award, 13. ↩
- Brent Dyck. (2010), Remembering Neville Chamberlain. Historian, (106), 13-14. Retrieved from http://proxyau.wrlc.org/login?url=https://search.proquest.com/docview/ 743881842? accountid =8285,14. ↩
- Mark Whitmore, “How Radar Changed The Second World War.” Imperial War Museums, May 24, 2018. https://www.iwm.org.uk/history/how-radar-changed-the-second-world-war. ↩
- Great Britain Air Ministry, and Hilary Aidan St. George Saunders. The Battle of Britain, August-October 1940: An Air Ministry Record of the Great Days from 8th August- 31st October, 1940 (London: H.M. Stationery Office, 1941). ↩
- Ibid. ↩
- Anthony J. Cumming, “Did Radar Win the Battle of Britain?” The Historian 69, no. 4 (2007): 688-705. Accessed February 5, 2020. www.jstor.org/stable/24453576, 2-3. ↩
- Ibid. ↩
- Geoffrey Wawro and Saul David, Greatest Events of World War II in Colour: The Battle of Britain (Netflix, 2019). ↩
- Cumming, 3. ↩
- Paul J. Maykish, “C2 rising: a historical view of our critical advantage.” Air & Space Power Journal, July-August 2014. Gale Academic OneFile (accessed February 5, 2020), 3. ↩
- Cumming, 3. ↩
- Ibid. ↩
- Brown, 109-111. ↩
- Royal Air Force Museum, (2018). Retrieved August 28, 2020, from https://www.rafmuseum.org.uk/research/online-exhibitions/history-of-the-battle-of-britain/radar-the-battle-winner.aspx ↩
- Maykish, 4. ↩
- Ibid. ↩
- Graham Allison, Destined for War: Can America and China escape Thucydides’s trap? (Melbourne, Australia: Scribe Publications, 2019), 1-3. ↩
- Jeffrey Engstrom, Systems Confrontation and System Destruction Warfare: How the Chinese People’s Liberation Army Seeks to Wage Modern Warfare. Santa Monica, California: RAND Corporation, 2018. https://www.rand.org/pubs/research_reports/RR1708.html. iii. ↩
- “Major Essay #1,” Iris’s ePortfolio, December 8, 2017; Xavier Vavasseur, “US Navy Declares IOC for MQ-8C Fire Scout VTOL UAV,” Naval News, July 9, 2019. ↩
- James Stavridis, ADM, USN (Ret.), “Naval Academy Leadership Conference 2020.” Naval Academy Leadership Conference 2020. January 21, 2020. ↩
- Donald J. Trump, 2017 National Security Strategy of the United States of America, 2017 National Security Strategy of the United States of America § (2017), 28. ↩
- Ben Buchanan, (2020, August 07). The U.S. Has AI Competition All Wrong. Retrieved August 27, 2020, from https://www.foreignaffairs.com/articles/united-states/2020-08-07/us-has-ai-competition-all-wrong. ↩
